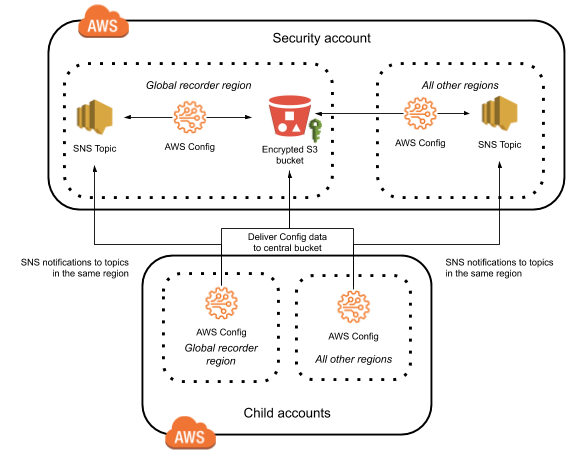
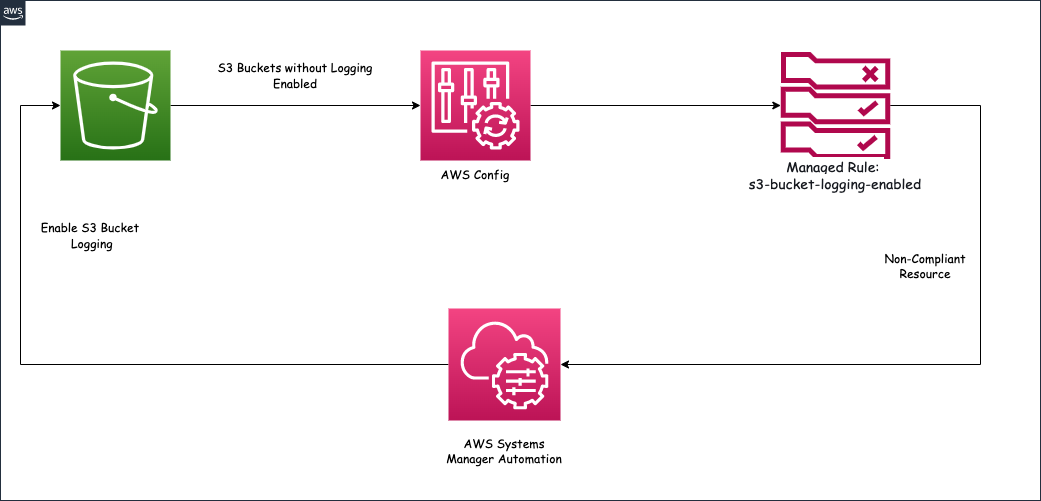
AWS Config to Monitor Non-Compliance S3 Buckets | by Duleendra Shashimal | FAUN — Developer Community 🐾
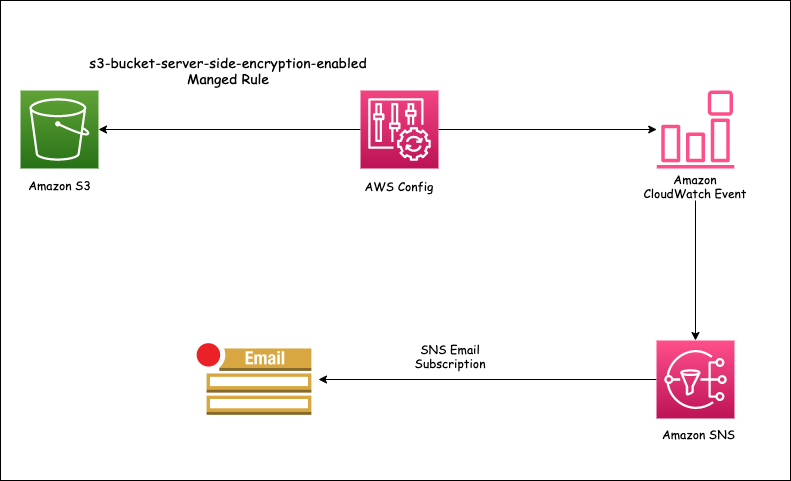
AWS Config to Monitor Non-Compliance S3 Buckets | by Duleendra Shashimal | FAUN — Developer Community 🐾

Automating organizational policies with custom AWS Config Rules and evidence collection in AWS Audit Manager | AWS Cloud Operations & Migrations Blog

Example Scenarios for AWS Config Continuous Monitoring of Amazon S3 Bucket Access Controls | AWS Cloud Operations & Migrations Blog

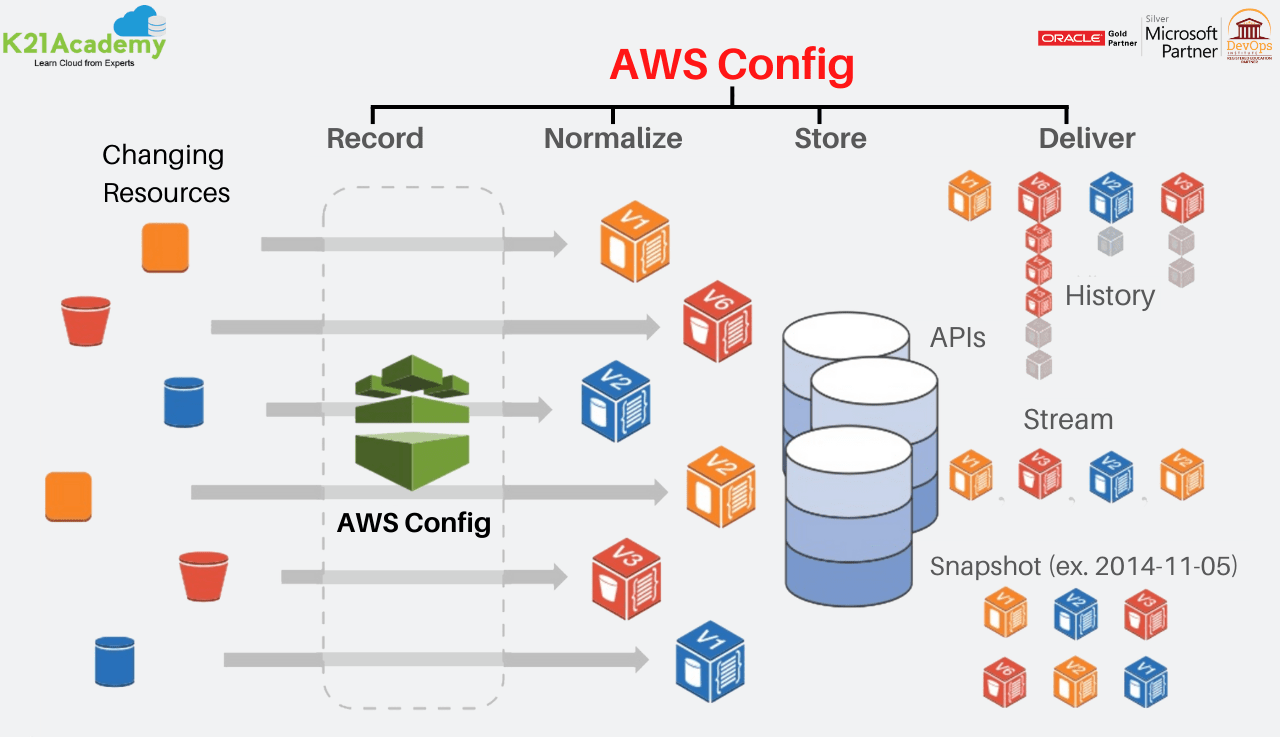
Using AWS Config for security analysis and resource administration | AWS Cloud Operations & Migrations Blog

How to Use AWS Config to Monitor for and Respond to Amazon S3 Buckets Allowing Public Access | AWS Security Blog

How to Use AWS Config to Monitor for and Respond to Amazon S3 Buckets Allowing Public Access | AWS Security Blog

How to Use AWS Config to Monitor for and Respond to Amazon S3 Buckets Allowing Public Access | AWS Security Blog

How to Use AWS Config to Monitor for and Respond to Amazon S3 Buckets Allowing Public Access | AWS Security Blog

How to Use AWS Config to Monitor for and Respond to Amazon S3 Buckets Allowing Public Access | AWS Security Blog

How to Use AWS Config to Monitor for and Respond to Amazon S3 Buckets Allowing Public Access | AWS Security Blog